Safeguarding industrial information – The need for secure data handling and transmission

Many companies have started exploring the benefits of accessing the Industrial Internet of Things (IIoT) and implementing Industry 4.0. As more and more data are accessed and shared between systems, data security must also be addressed. Guidance is provided by organizations such as the Open Web Application Security Project (OWASP). The review below is about Amorph Systems’ SMARTUNIFIER product and the measures in place to address reliability and security during the product’s lifecycle. This includes adherence to specifications and measures to ensure the highest level of protection is implemented for the credentials of the participating systems and the data that is transmitted.
SMARTUNIFIER has a fully decentralized architecture that enables quick and easy integration of shopfloor equipment, edge devices, and IT-systems without the requirement to deploy central platforms and databases. Communication is from one or multiple data sources to one or multiple data receivers in massively scalable topologies. SMARTUNIFIER communication instances are typically operated directly on-premise (e.g., on Industrial PCs, Edge Gateways) or run within containerized environments (e.g., Docker, Cloud), thereby effectively isolating the data exchange services that they provide to avoid any interference with other services.
The diagram below illustrates the architecture.
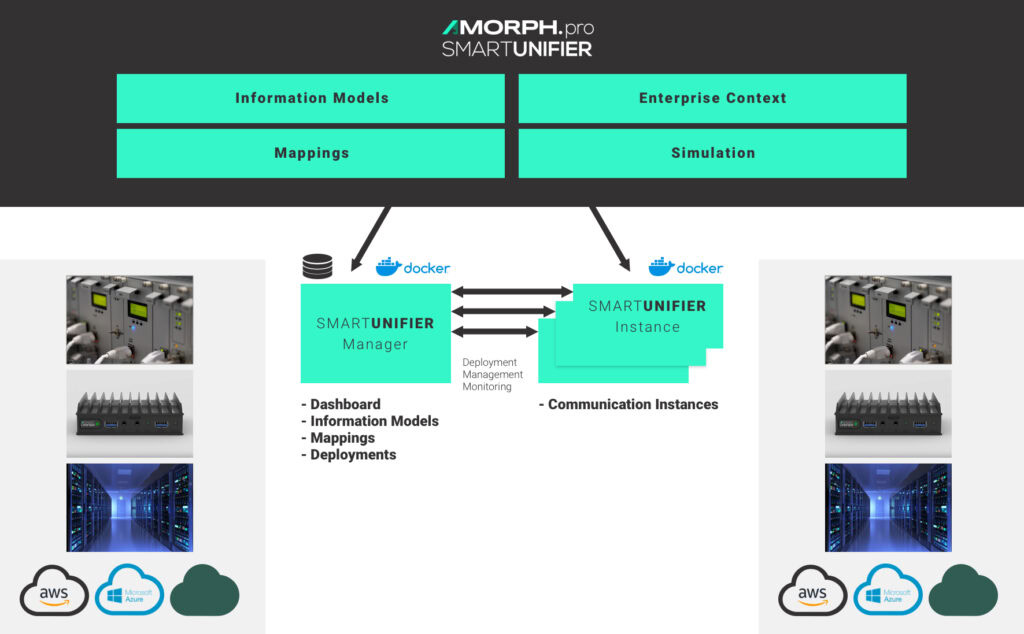
Multiple decentralized Communication Instances can be deployed anywhere and managed by the SMARTUNIFIER Manager, including real-time monitoring and logging of deployed Communication Instances. Industrial connectivity can be realized with any device or system communication protocol and any data format.
Reliability and Security in the Development Lifecycle
It is imperative that security, as well as reliability, are already addressed during the product’s development phase. To this end, Amorph utilizes state-of-the-art software development platforms and tools. Building, testing, and deployment are automated using Jenkins Automation Server to facilitate continuous integration and delivery. To ensure code quality, continuous testing is conducted starting with unit tests for individual modules, integration tests to ensure interoperability of components, and end-to-end tests to ensure the integrity of the application. Testing has been automated, and build-checks are executed daily.
In addition to following industry standards and guidelines, specific tools are also used to test code quality and scan for security vulnerabilities.
- Sonarqube is used to ensure the maintainability, reliability, and security of the code. With regular scans, potential quality or security issues are detected early and addressed promptly to provide high-quality, secure code.
- OWASP Dependency-Check is used to detect publicly disclosed vulnerabilities contained within the SMARTUNIFIER project’s dependencies to reduce risk in the software supply chain. Dependency-Track leverages a Software Bill of Materials (SBOM) capabilities to conduct composition analysis that traditional Software Composition Analysis (SCA) solutions cannot achieve.
- All software components are continuously updated with the latest security patches.
- OWASP Zed Attack Proxy (ZAP) is used for penetration testing of SMARTUNIFIER to detect vulnerabilities to malicious attacks.
Connectivity, Configuration, and Deployment
Configuration, deployment, and management of SMARTUNIFIER Instances is done using SMARTUNIFIER Manager. All configuration data is fully encrypted, unlike some simpler solutions, that store credentials as plain text within configuration files. Individual user authentication is supported and Windows AD / LDAP integration is available. SMARTUNIFIER Manager makes it easy to deploy updates to the communication instances in the production environment so that integrity and security can continually be maintained.
The diagram below illustrates security measures that are implemented with a SMARTUNIFIER deployment.
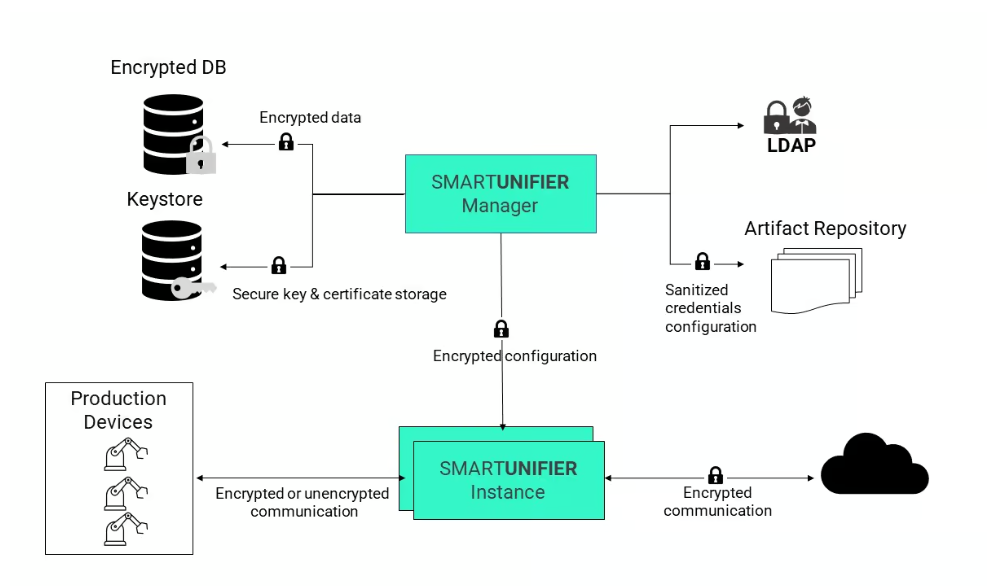
In some cases, at the shopfloor level, encryption is not supported by the protocols of legacy equipment. SMARTUNIFIER can simultaneously handle encrypted and unencrypted communication and provides a way to introduce secured protocols for upper-level communication, as described in the next section.
Reliable and Secure Operation
Secure operation of interfaces starts with having all the identity and access management functions described above in place. SMARTUNIFIER enables multiple vertical and horizontal connections between systems, and access can be secured with encrypted credentials and private key and identity certificates presented to both connecting parties for verification. The use of encryption and certificates is implemented for all industrial protocols enabling secured connections such as secured MQTT, secured OPC-UA, and others.
Linux or Windows computer units provide the connectivity nodes where SMARTUNIFIER is deployed for on-premise or edge deployments. Data may be stored temporarily on these HW devices as logs or for buffer (cache) purposes. This temporary data is protected by assigning the hardware with appropriate access rights and user roles.
SMARTUNIFIER can also be used to introduce secured protocols where unsecured data streams exist by deploying locally near shopfloor equipment or devices and mapping any unsecured equipment/device interface into a secured protocol (e.g., OPC-UA, MQTT). This way, “unsecured data streams” coming from shopfloor equipment/devices can be transferred to any northbound system in a secured manner by isolation of the equipment/devices. The same principle can also be applied when sending control parameters (e.g., parameters for automatic screwdrivers, NC programs, recipes, …) or commands from a northbound system to the equipment/device. This is illustrated in the diagram below.
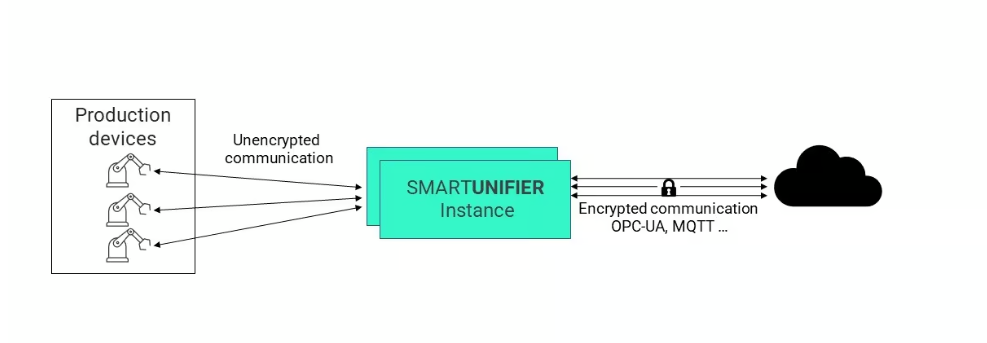
Containers are used to isolate SMARTUNIFIER instances from Operating Systems resources at runtime. During operation, data integrity is protected with checksums ensuring that data is not lost or altered during transmission, and end-to-end transport encryption can be implemented to protect the transmitted content. All of these measures ensure that a high level of security is maintained during runtime. For operations monitoring, SMARTUNIFIER creates detailed logs for all communication and other activities it performs. Integrating with external security supervision or monitoring systems (e.g., Splunk) and providing online log files via a dedicated monitoring communication channel is possible, further ensuring the integrity of communication processes and enabling early detection of intrusions.
Conclusion and Benefits
Industrial data exists in different components and systems, in various formats, with separate access protocols. To harness this data’s power and benefit from the synergies of system-wide interoperability, we must effectively digitize shopfloor data and deliver the content quickly, reliably, and securely. As described above, security is a central theme for SMARTUNIFIER. With adherence to standards and utilization of best-of-breed technology and tools during the development lifecycle, during configuration and deployment, and during operation, steps are continuously taken to ensure the reliability, integrity, and security of data.
With SMARTUNIFIER, your industrial operation can easily and affordably implement secure communication with shopfloor equipment and throughout the enterprise.
